Unlock the secrets of your vehicle’s data with CAN bus sniffing. This comprehensive guide provides a practical, step-by-step approach to reverse engineering CAN data using the CLX000 CAN bus sniffer, SavvyCAN, and Wireshark. Learn how to decode proprietary information, extend DBC databases, and unlock new possibilities for vehicle data analysis and control.
Why Sniff the CAN Bus? Benefits of Reverse Engineering
Sniffing the CAN bus, or reverse engineering vehicle data, offers several compelling advantages:
-
Decoding Proprietary Data: Uncover hidden vehicle parameters and functionalities not accessible through standard OBD2 protocols.
-
Extending DBC Databases: Enhance existing CAN database files (DBCs) by adding newly discovered signals and messages.
-
Unlocking New Use Cases: Gain insights into vehicle behavior, optimize performance, and develop custom applications based on real-time data.
-
Enabling Vehicle Control (Advanced Users): With careful analysis, potentially control vehicle functions by sending specific CAN frames. Proceed with caution as improper commands can have unintended consequences.
How to Sniff the CAN Bus: A Step-by-Step Guide
Reverse engineering CAN data involves a systematic process:
-
Identify the Target Signal: Determine the physical action or parameter you want to monitor (e.g., windshield wipers).
-
Isolate the CAN ID: Use a CAN bus sniffer (like the CLX000) and software (SavvyCAN or Wireshark) to capture live CAN data. Observe changes in data while manipulating the target signal to pinpoint the relevant CAN ID. Two methods for isolating the CAN ID include real-time data streaming and logging data to an SD card for later analysis.
-
Pinpoint the Signal Bits: Analyze the data bytes within the identified CAN ID. Observe which bits change in response to the target signal, noting their position and length.
-
Determine Scaling and Offset: Calculate the scaling factor and offset required to convert the raw signal value into a meaningful physical value. This involves observing the raw data values at known minimum and maximum physical values.
-
Document Your Findings: Record the CAN ID, bit position, length, scaling, and offset in a DBC file for future use.
Reverse Engineering with SavvyCAN and Wireshark
SavvyCAN offers powerful features for sniffing the CAN bus:
- Real-Time Data Streaming and Filtering: Monitor live CAN data, filter by CAN ID, and easily identify changes in data bytes and bits.
- Sniffer View for Discrete Events: Quickly analyze unique CAN frames and highlight changing data, making it easier to correlate physical events with CAN data.
- Range State View for Continuous Data: Analyze logged CAN data, test hypotheses about signal location and scaling, and compare with benchmark data.
- Live Transmit Functionality: (Advanced Users) Send custom CAN frames to test vehicle responses. Exercise extreme caution when using this feature.
- DBC Editor: Create and modify DBC files to decode and organize your reverse-engineered data.
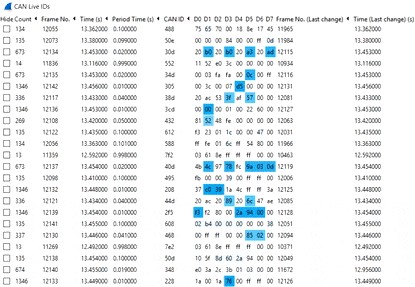
Wireshark, with the CAN Live plugin, provides a trace view of unique CAN IDs, highlighting changes in data bytes for efficient analysis.
The CLX000 CAN Bus Sniffer: Your Essential Tool
The CLX000 is a versatile and affordable CAN bus data logger and interface:
- Plug and Play: Easy setup and configuration with free software tools.
- Standalone Logging: Log data to an SD card for extended periods without a PC.
- Real-Time Streaming: Stream live data to SavvyCAN or Wireshark for analysis.
- Compact and Affordable: A powerful tool at a fraction of the cost of less specialized solutions.
Conclusion
Sniffing the CAN bus with the CLX000 and powerful software like SavvyCAN and Wireshark opens up a world of possibilities for understanding and interacting with your vehicle’s data. By following this guide, you can successfully reverse engineer CAN data, decode proprietary information, and unlock new insights into your vehicle. Remember to always proceed with caution, especially when attempting to control vehicle functions.