It was just a month ago when I became another statistic – my car, a Mercedes-Benz, vanished from my driveway in the dead of night. As a cybersecurity journalist with nearly two decades in the field, I’ve written extensively about car hacking. Yet, I’d fallen into the common trap of feeling disconnected from the reality of cyber threats, believing “it won’t happen to me.” I was wrong.
Like hundreds of thousands of others in the UK annually, I became a victim of car theft. However, my profession offered a unique angle: access to experts who could explain exactly how my car was stolen and, crucially, highlight the increasing role of tools like diagnostics boxes in modern vehicle theft.
The Stark Reality of Car Theft: Numbers Don’t Lie
Recent figures from the DVLA paint a grim picture: a car is stolen in the UK approximately every eight minutes. The Office of National Statistics reveals an even more alarming number – 397,264 cars stolen in England and Wales between October 2022 and September 2023. This figure, much higher than media reports often suggest, underscores the scale of the problem.
Luxury brands like Land Rover and Mercedes-Benz are disproportionately targeted, becoming unwanted leaders in car theft statistics. Recovery rates are dismal, with most data suggesting less than 20% of stolen vehicles are ever recovered.
The crucial question is: how are these thefts occurring with no signs of forced entry, vehicles disappearing silently into the night?
Was My Car Hacked? Decoding the Method
My stolen car was a Mercedes-Benz GLC 220 AMG Line Premium D, equipped with keyless entry and start. The detective on my case informed me that within a small radius of my home, six similar high-value cars were stolen over just two nights. Law enforcement suspects organized crime groups operating from major cities were responsible.
Finding my driveway empty one morning was a shock. Both car keys were inside my house, undisturbed. There was no broken glass, no sign of forced entry. My initial thought, given my background, was: “My car has been hacked.”
Cybersecurity experts largely agreed. Graham Cluley, of the Smashing Security podcast, defined hacking broadly as “gaining unauthorized access,” which perfectly described the theft. David Rogers, CEO of Copper Horse, a connected car security specialist, concurred, labeling it “almost certainly car hacking.”
However, Adam Pilton, a former police officer and now cybersecurity consultant at CyberSmart, offered a nuanced perspective. He suggested a “relay attack” as the likely method, a simpler yet effective technique, especially given the multiple thefts in the area. Ivan Reedman from IOActive provided a further distinction, arguing that while unauthorized access was gained, it might be technically “theft vs. a hack” as no data was accessed in the system itself, merely physical access to the vehicle.
Relay Attacks: The Silent Car Thief
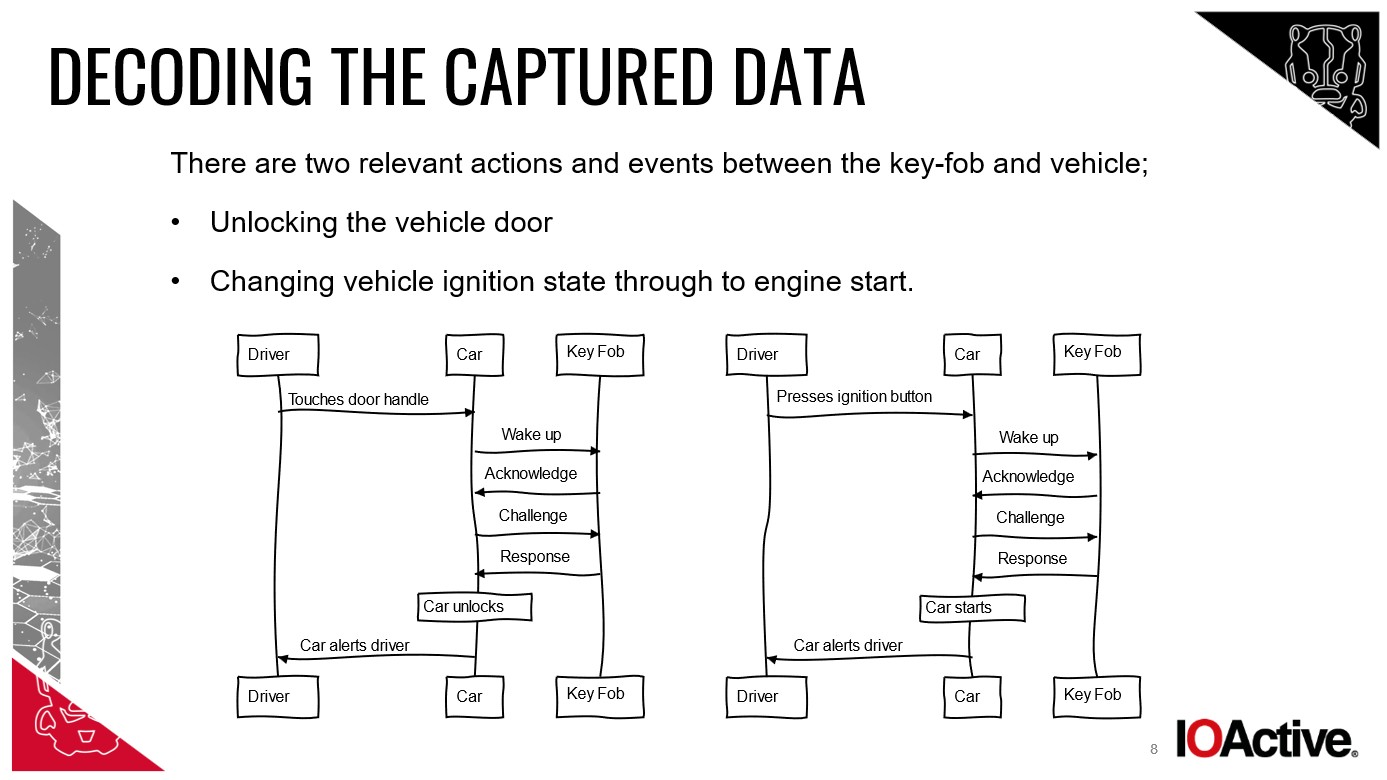
Despite varying definitions, the consensus among experts was that a relay attack was the most probable method used to steal my car. My Mercedes featured ‘passive entry passive start’ (PEPS), allowing entry and ignition as long as the key fob was nearby.
Chris Pritchard, a principal adversarial engineer at Lares, explained the mechanics: thieves use “a tool and aerial to relay the signal broadcast between your contactless key and the car. The car is tricked into thinking the key is close and unlocks the door.”
William Wright, CEO at Closed Door Security, detailed the two-device setup: one device near the house to capture the key fob signal, even through walls, and another by the car to relay that signal. These devices typically need to be within 10-15 meters of the key and can execute the theft in as little as 30 seconds.
Understanding the relay attack process: signal interception and vehicle access.
Reedman, who even demonstrated a relay attack for the BBC using readily available components, emphasized its simplicity: “Relay attacks are one of the simplest attacks, requiring no [technical] knowledge or secrets.”
Once the car is started via a relay attack, a new challenge arises for the thieves: how to keep it running and operational after the initial signal relay? This is where the on-board diagnostics (OBD) system becomes critical.
The Role of On-Board Diagnostics (OBD) in Car Theft
While a relay attack grants initial access and allows starting the engine, it doesn’t solve the long-term control of the vehicle. Most cars, once started, will continue running even if the key signal is lost, but they often cannot be restarted without the key being present. This is a safety feature to prevent engine stall if a key battery dies while driving.
To overcome this limitation and gain full control, thieves target the on-board diagnostics (OBD) port. David Rogers explained, “Access to the OBD will trigger the car into starting by using other devices. Once the car is fooled into thinking the driver has legitimate access, there’s no reason to prevent driving.”
The OBD port, typically located under the steering wheel, is designed for garage mechanics to diagnose issues and reset systems. However, it also provides a gateway to the car’s computer system, allowing for key programming and system manipulation.
Chris Pritchard elaborated, “It’s a little port normally underneath the steering wheel, just to the right. Garage mechanics use it for diagnostics and resetting warning lights, for example.” He suspects that in his own Audi theft, “they broke in and programmed a new key with an OBD tool so they could open, close and start the car as needed. There’s a good chance something similar happened here.”
This is where the “diagnostics box” comes into play. Thieves use specialized OBD programming tools, often readily available online, to connect to the OBD port. These tools can be used to:
- Program new keys: Overriding the original keys and registering new ones, effectively giving the thieves permanent access and control. This bypasses the need for the original key fob after the initial relay attack start.
- Disable security features: Potentially deactivating alarms, immobilizers, or tracking systems, making the car easier to steal and harder to recover.
- Unlock car doors: While less direct than key programming, some sophisticated OBD tools might even offer functionalities to unlock doors or manipulate central locking systems. This is less about “unlocking” after initial theft and more about ensuring continued access and control.
Therefore, while relay attacks are often the initial entry point, the OBD port and diagnostics boxes are crucial for thieves to permanently unlock car doors and gain full, long-term control of the stolen vehicle. This explains why focusing on “How To Unlock Car Doors With Diagnostics Box” is so relevant – it highlights a critical stage in modern car theft beyond just initial entry.
Debunking the Flipper Zero Myth
Initially, after sharing my car theft story, some experts suggested a Flipper Zero might be involved. This handheld device, capable of various wireless signal manipulations, has been controversially linked to car theft.
The Flipper Zero device, often mistakenly linked to sophisticated car theft techniques.
However, for my specific case and the broader method of theft described, experts deemed Flipper Zero involvement “highly improbable.” Chris Pritchard dismissed the Flipper Zero theory, referencing the Canadian government’s ban on the device due to its alleged role in auto theft. While powerful for various tasks like vulnerability testing and signal cloning, the Flipper Zero is not typically associated with the relay attacks and OBD-based key programming used in sophisticated car thefts.
Who Are These Car Thieves? Skill and Accessibility
The techniques used to steal keyless cars, especially relay attacks and OBD programming, are not closely guarded secrets. “The technique is well known by car thieves, and there’s plenty of information about how to do it online,” explained Graham Cluley.
David Rogers emphasized the ease of access to car theft equipment: “Car theft equipment is astonishingly easy to get hold of. The majority of car thieves have no technical knowledge; they push a button on a box or wave an antenna, and the car unlocks.” The real expertise lies higher in the criminal chain, in the development and supply of these tools.
Adam Pilton added that the tools themselves are often repurposed from legitimate uses, like communication systems or wireless range extenders. Criminals simply adapt and misuse them. Ivan Reedman went further, arguing that using relay and OBD tools “requires no skill,” potentially involving just watching online videos and purchasing readily available equipment.
Shockingly, reports indicate even children as young as 10 are being arrested for car theft, highlighting the accessibility and simplicity of these methods.
Manufacturer Response and Accountability
With car theft rising and keyless entry systems being prime targets, manufacturers face increasing pressure to enhance security. However, William Wright believes “the automotive industry is far behind most in protecting against technological attacks.”
Mercedes-Benz, in response to inquiries, stated that security is a “top priority.” They highlighted that from mid-2019, GLC models received motion sensors in key fobs, deactivating keyless go when stationary to prevent relay attacks. My 2018 model, unfortunately, missed this update. They also mentioned the option to manually disable keyless go and a “stolen vehicle help” function via their Mercedes me app.
Older models often lack modern security features against relay attacks and OBD theft.
However, critics argue manufacturers prioritize convenience over security. Chris Pritchard noted, “Car manufacturers continue to push ease-of-use functionality over security.” David Rogers pointed out a lack of urgency and a tendency to blame victims, rather than fully addressing the vulnerabilities in their systems.
Despite this, manufacturers are making some advancements, including motion sensors in key fobs and positioning technology to verify key proximity. However, making customers aware of keyless entry risks at the point of sale remains a crucial, often missed, step.
Legal Measures and the Criminal Justice Bill
The UK’s Criminal Justice Bill, introduced in 2023, aims to criminalize the possession of electronic devices used for vehicle theft, including signal jammers. This is a step towards tackling the tool availability issue.
However, concerns exist within the security research community that such legislation could hinder legitimate research into vehicle security vulnerabilities, as security researchers might face arrest for using these technologies for testing and improvement purposes.
The Appeal of “Dumb Cars” and Prevention
Relay attacks and OBD-based theft are attractive to criminals due to their low risk and lack of visible damage. “It’s a low-risk crime that causes no damage to the stolen vehicle, which keeps the resale value high for the criminal,” explained Chris Pritchard.
Pilton noted that while traditional key-based systems have weaknesses, keyless entry presents new vulnerabilities to specific attack methods. This leads some, like Graham Cluley, to express a preference for “dumb cars” without keyless entry.
The scale of keyless car theft is vast, recovery rates are low, and prosecutions are rare.
Prosecution Challenges and Recovery
Wright described prosecution success rates as “very poor” due to the speed and stealth of these thefts. Cars are often quickly moved out of the country or dismantled in “chop shops” for parts.
Modern car theft is often silent and leaves no trace of forced entry.
Pilton, from his law enforcement experience, highlighted the difficulty in identifying perpetrators, even when cars are located. Often, only evidence linking stolen cars to broader organized crime groups is found, making direct prosecution for individual car thefts challenging.
My own car remains missing, likely destined for overseas or a chop shop. While the investigation continues, hope for recovery is minimal.
Securing Your Keyless Car: Practical Steps
Having experienced car theft firsthand, I sought advice from experts on how to protect keyless vehicles. The most consistent recommendation was: Faraday.
“Use a Faraday box or wallet to block any signal being sent or received by your car keys and get into the habit of always putting your keys in such a box when you return home,” advised Cluley. This blocks relay attacks by preventing signal interception.
Reedman emphasized testing Faraday solutions to ensure effectiveness. He also recommended storing keys far from the car and front door.
Rogers suggested disabling keyless ignition if possible, using mechanical steering locks, and crucially, considering an OBDII port lock. This physical lock prevents unauthorized access to the OBD port, hindering key programming and other OBD-based theft methods.
Pilton stressed the importance of raising awareness to empower car owners to take preventative measures.
Other security measures include:
- Steering wheel locks: A visible deterrent and physical security measure.
- Immobilizers and alarms: While potentially bypassed by sophisticated thieves, they still offer a layer of security.
- Tracking devices: Can aid in recovery, though thieves often disable these.
- Car insurance: Essential to mitigate financial loss in case of theft.
In conclusion, understanding how thieves unlock car doors with diagnostics boxes, often after an initial relay attack, is crucial for car owners. By implementing security measures like Faraday boxes, OBD port locks, and steering wheel locks, and by demanding greater security focus from car manufacturers, we can collectively make it harder for criminals to exploit these vulnerabilities and protect our vehicles from modern theft techniques. Until then, vigilance and proactive security measures are our best defense.