Vultur, a sophisticated Android banking malware known for its screen recording capabilities, has undergone significant updates, enhancing its remote control functionalities and employing advanced evasion techniques. This analysis delves into Vultur’s evolution, examining its infection chain, new features, obfuscation methods, execution flow, and command-and-control (C2) communication. Understanding these changes is crucial for effective Dfox It strategies – detection, forensic analysis, and incident response.
Enhanced Remote Control: Beyond Screen Recording
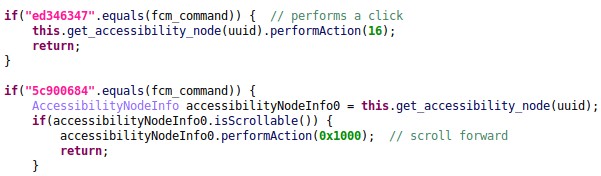
Vultur now leverages Android Accessibility Services, enabling granular remote control of infected devices. The malware operator can issue commands via Firebase Cloud Messaging (FCM) to perform actions like clicks, scrolls, swipes, and volume control, providing more flexibility than the previous AlphaVNC and ngrok implementation. A new file manager functionality allows for downloading, uploading, deleting, installing, and searching files, further expanding the attacker’s control. The ability to block specific apps from running, coupled with displaying custom HTML content, adds another layer of manipulation. These advancements signify a shift towards comprehensive device takeover, enabling attackers to execute a wider range of malicious activities.
Evasion Techniques: Staying Under the Radar
Vultur incorporates several techniques to evade detection and hinder analysis. All C2 communication now employs AES encryption and Base64 encoding, masking malicious traffic from network security solutions. The dropper, disguised as a legitimate McAfee Security app, exhibits a low detection rate on VirusTotal, highlighting the effectiveness of this social engineering tactic. Utilizing the official Android Accessibility Suite package name for its malicious Accessibility Service further contributes to its stealth. The use of native code for payload decryption and the distribution of malicious code across multiple payloads complicate reverse engineering efforts, making dfox it more challenging.
Infection Chain and Execution Flow: A Multi-Stage Attack
The infection chain begins with a hybrid attack involving SMS messages and a phone call, leading victims to install the trojanized McAfee Security app (Brunhilda dropper). This dropper then deploys three Vultur payloads in a layered approach. Payload 1 focuses on obtaining Accessibility Service privileges and installing Payload 2. Payload 2 sets up AlphaVNC and ngrok, handles HTML injections, and decrypts Payload 3. Payload 3, a DEX file, contains the core malicious functionality and interacts closely with Payload 2. This multi-stage architecture allows for modularity and obfuscation, making it difficult to grasp the full extent of the malware’s capabilities from a single component. This complexity necessitates a thorough dfox it process to uncover the complete infection chain.
C2 Communication: A Deeper Dive
Vultur communicates with its C2 server using JSON-RPC 2.0 over HTTPS for tasks like bot registration and configuration retrieval. FCM is used for delivering commands to the infected device. The latest version introduces new C2 methods for functionalities like file management (vnc.fm), pattern extraction (vnc.pattern), and blocked package management (vnc.blocked.packages). Numerous new FCM commands facilitate the expanded remote control features, such as app control, screen manipulation, and keyboard management. Analyzing this communication is critical for understanding the attacker’s capabilities and intentions, a core aspect of dfox it.
Conclusion: The Need for Proactive Defense
Vultur’s ongoing evolution underscores the need for robust mobile security measures and proactive dfox it strategies. Its advanced remote access capabilities, coupled with sophisticated evasion techniques, pose a significant threat to Android users. Security professionals must stay vigilant, adapting their detection and response methods to counter these evolving threats. Understanding Vultur’s latest tactics, techniques, and procedures is paramount for effective defense.
Figure 1: Vultur’s infection chain, showcasing the multi-stage deployment process.
Figure 2: Example of Vultur’s AES encrypted and Base64 encoded C2 communication.
Figure 3: Code snippet demonstrating Vultur’s abuse of Accessibility Services for blocking apps.