Car theft is a growing concern, with sophisticated methods leaving vehicle owners vulnerable. While the idea of car hacking might sound like something from a movie, the reality is often simpler, yet equally effective. This article delves into the world of relay attacks, a common technique used by thieves, essentially acting as an “extension tool” to unlock car doors and drive away without a trace of forced entry. Understanding how these tools work is the first step in protecting your vehicle.
The Shocking Reality of Modern Car Theft
It might be unsettling to think about, but in many parts of the world, a car is stolen at an alarming rate. Recent statistics highlight that hundreds of thousands of vehicles are stolen annually, a number often underestimated in public perception. Luxury brands and popular models are frequently targeted, making them unwanted “winners” in theft statistics. Recovery rates are discouragingly low, meaning once your car is gone, it’s likely gone for good. The question then arises: how are these thefts occurring so seamlessly, often without any sign of forced entry?
Decoding the Relay Attack: The “Extension Tool” in Action
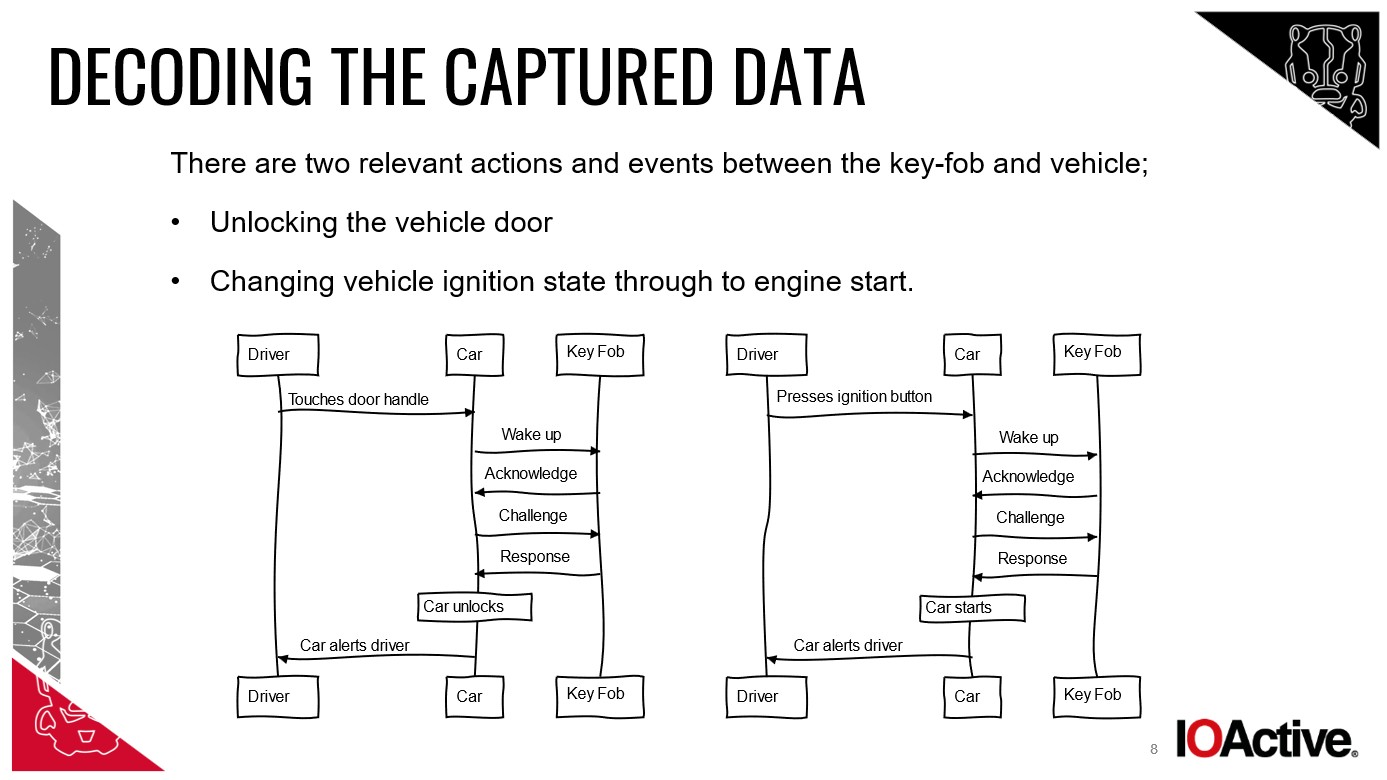
For many modern cars equipped with keyless entry and start systems (Passive Entry Passive Start – PEPS), the vulnerability lies in relay attacks. Imagine your key fob as a transmitter and your car as a receiver. Normally, a short-range signal is exchanged when you are close to the car, allowing you to unlock and start it. A relay attack exploits this system using what we can consider an “extension tool” – a device that amplifies and relays the key fob’s signal to the car, even if the key is far away inside your house.
Cybersecurity experts explain that this “extension tool” typically involves two devices. One device, positioned near your house, acts as a receiver to capture the faint signal emanating from your key fob. The second device, held near the car, then transmits this relayed signal, tricking the car into thinking the key is nearby. This entire process can take as little as 30 seconds, allowing thieves to silently unlock, enter, and start your car. Effectively, the relay attack tool extends the operational range of your keyless entry system, bridging the distance between the key and the car.
Beyond Entry: What Happens After Unlocking?
While the relay attack “extension tool” grants thieves access and allows them to start the engine, a crucial question remains: how do they continue driving when the key is no longer present? The answer lies in vehicle safety design. For safety reasons, most cars will not shut off the engine if the key signal is lost after starting. Imagine if your car engine suddenly died while driving because of a low key battery – it would be dangerous. Therefore, once the engine is running, it will continue until it is manually turned off.
This is where the thieves’ methods evolve. Often, after driving the stolen vehicle to a safe location, they gain access to the car’s On-Board Diagnostics (OBD) port. This port, usually located under the steering wheel, is designed for mechanics to diagnose and service vehicles. However, in the wrong hands, OBD access allows criminals to use programming tools to disable your original keys and potentially program a new key, ensuring they have full control over the vehicle even after the engine is switched off and restarted.
Debunking Myths: Relay Attacks vs. Other Methods
Initially, when car theft incidents occur, terms like “car hacking” or specific devices like “Flipper Zero” might be mentioned. While technically a relay attack could be considered a form of “hacking” in its broadest sense (unauthorized access), cybersecurity experts differentiate it from sophisticated data breaches. Relay attacks, using these “extension tools,” are surprisingly simple and do not necessarily involve deep technical knowledge.
Similarly, while devices like Flipper Zero are capable tools for various wireless signal manipulations, experts argue they are not typically the primary tool used in relay attacks for modern car theft. The core of a relay attack is signal extension and amplification, achievable with simpler, readily available equipment. The focus should remain on understanding the vulnerability of keyless entry systems to signal relaying, regardless of specific device names.
Who Are the Perpetrators and How Do They Acquire These “Tools”?
The ease of execution of relay attacks is concerning. The knowledge and equipment needed are surprisingly accessible. Information on how to perform relay attacks is available online, and the “extension tools” themselves are often repurposed communication devices or easily obtainable electronic components. This means the barrier to entry for car theft using relay attacks is relatively low.
Reports even indicate that individuals with limited technical skills, and in some cases, even children, are involved in car thefts. This highlights that the complexity lies not necessarily with the individuals carrying out the theft, but potentially higher up in organized crime rings who develop, supply, and distribute these “extension tools” and coordinate the operations. The individuals performing the theft might simply be following instructions and using pre-configured devices.
Manufacturer Response and Accountability
With the rise in keyless car thefts via relay attacks, the spotlight turns to car manufacturers. Are they doing enough to address these vulnerabilities? While some manufacturers emphasize their commitment to vehicle security and point to updates like motion sensors in key fobs (deactivating keyless go when stationary) as improvements, questions remain about the speed and proactiveness of the automotive industry in tackling these issues.
Some argue that manufacturers prioritize convenience features like keyless entry over robust security measures. There’s also a perception that the industry is slow to acknowledge and respond to evolving theft techniques. While updates like motion sensors are a step forward, they are often introduced in newer models, leaving older keyless entry vehicles vulnerable. Furthermore, options like disabling keyless go functionality are not always prominently presented to customers at the point of sale, limiting owner awareness and control over their vehicle’s security settings.
Protecting Your Keyless Car: Practical Steps
Despite the vulnerabilities, car owners are not powerless. Several practical steps can significantly reduce the risk of relay attack theft. The most consistently recommended advice is to use a Faraday box or pouch. These specially designed containers block electromagnetic fields, preventing your key fob from transmitting signals when stored inside. Think of it as creating a signal “dead zone” for your keys when you are at home.
Ensuring your spare key is also protected in a Faraday box is equally important. Additionally, verifying the effectiveness of your Faraday solution is advisable – test if your car unlocks when the key is inside the box. Beyond Faraday protection, physical deterrents like steering wheel locks and OBD port locks add further layers of security. Some older, simpler methods, like parking strategically to block your keyless car with a non-keyless vehicle, can also offer a degree of protection.
The Role of Legislation and Future Security
Legislative efforts, like the introduction of bills to criminalize the possession of electronic devices used for vehicle theft, signal a growing recognition of the problem at higher levels. However, concerns exist within the security research community that overly broad legislation might hinder legitimate security research aimed at uncovering and mitigating vulnerabilities.
Ultimately, a multi-faceted approach is crucial. Manufacturers need to prioritize security alongside convenience, proactively developing and implementing robust security measures. Law enforcement needs to target not just the individuals carrying out thefts, but also the organized networks and suppliers of “extension tools” and other theft equipment. And car owners need to be informed and empowered to take practical steps to protect their vehicles. Until then, understanding the mechanics of relay attacks and the “extension tools” used by thieves is a vital part of staying one step ahead in the ongoing challenge of car security.